Decentralised Model in Detail - Defence
Next: Component Model and Summary
Defence
On decentralised and digital world defence need to be rethought. Reactive defence where actions are taken only when something bad happens, does not work. If a perpetrator gains access to systems, they can block access from outside, change logs to hide their actions, leave hard to remove digital viruses around and so on.
Defence thinking needs to be flipped on its head. Systems need to be stress tested before this happens. Systems means both people and computers.
You need to be your own worst enemy.
There are actions to be done long before anything happens, during and after.
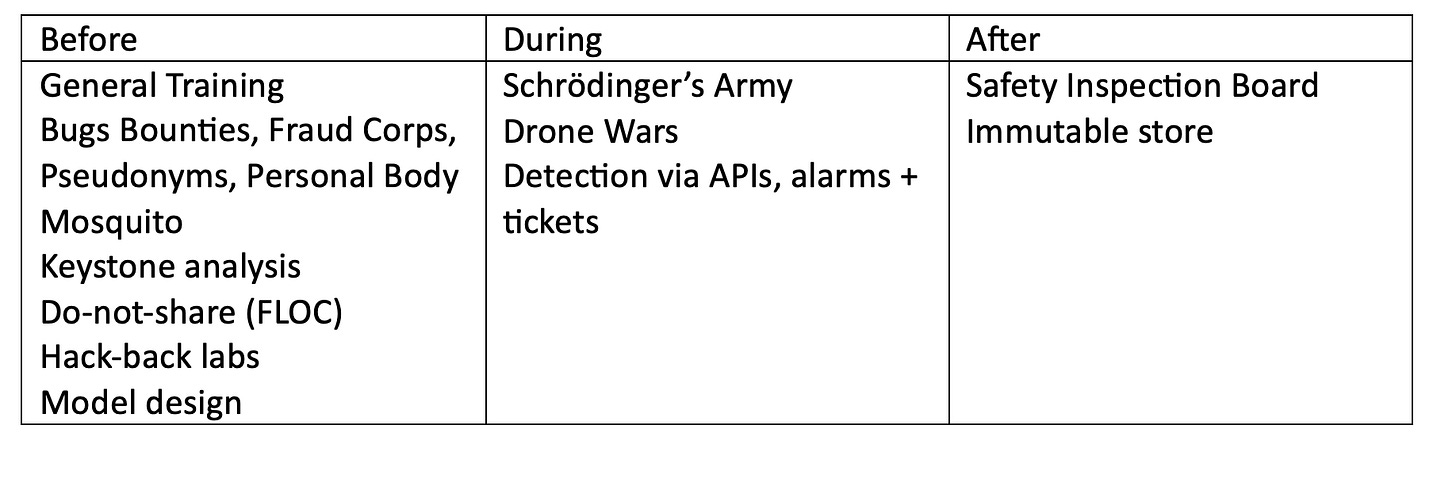
Before
General training of people on security in schools and in general is self-evident and goes into the pre-steps.
Fraud Corps is a method of testing people’s gullibility in production. It is a unit of public side that tries to trick citizens into clicking links that lead them to forged web sites asking for bank details as an example. Rather than losing your life’s saving, the fraud corps return everything.
Bugs bounties are programs where public rewards are offered to anyone who gains access to systems without proper authorisation if they reveal how they did it. Privacy bounties are similar concept where payment is for data errors (leaks of privacy data, injections of bad data etc.).
These are ways to gain resilience by adding stress to system to make it stronger. Similar to our body becomes stronger after each disease.
See here more on bugs bounties, Citizen’s Right To Audit the Government and also Safety Investigation Authority (post-step)
Part of defence is also to keep data local as much as possible. The federated learning of cohorts (FLOC) mechanism is a way to implement machine learning models without revealing user data. Its based on sharing locally trained models rather than underlying data.
Another approach is to add random errors in a way that do not change statistical properties of larger group.
(For alternate view on FloC see this )
Tech rank and alpha, beta and gamma diversity are mechanisms for understanding how big problem monocultures are and where the weak spots are on system level. Keystone analytics highlights areas that are most important in terms of technologies, raw materials, companies etc. It allows to focus on right areas for improvement.
Hack back labs is a service of hacking into adversarial nations systems to see how much intellectual property they have stolen, how they do it and what they are currently doing. Then planning actions based on that.
People will carry their personal on body cameras or have a drone monitoring their environment all the time. This way if something happens, at least the perpetrator is easy to identify. This concept is called “personal body mosquito”. The risk of getting caught protects to a degree. See more on both hack back labs and personal body mosquito
On the digital world people will use pseudonyms to protect them from mob-rule so common today.
During
Future physical conflicts will be fought with drones and automated robots as human reaction times are simply too slow. They can be produced on-demand when needed in decentralised manner. This means the army is summoned when needed, otherwise it lays dormant as a storage tiger on local bitbuckets (disks). This army can be upgraded for free and thus has always the latest defence systems at its disposal. This is the Schrödinger’s Army. It exists and does not exist at the same time. This defence can be built on independent areas that make their own selection of robots, drones and other decisions. All defence areas having same solution would create a single point of failure (SPoF) in case there is a backdoor or other security vulnerability,
Not doing anything until need emerges, makes upkeep and upgrade cheap. A problem persists how to reliably know that an attack is underway given the increased speed of action. This can be at least to a degree solved by having a fleet of so-called oracles (services that report status) and randomly asking some of them of the situational status. The selection is based on reputation. Different areas need to use different detection agents. Also the communications mechanism between oracles and the final decision needs to be reliable. Alternate secure mechanisms may need to be developed. One area for example where ultimate reliability is needed, are the nuclear launch procedures. Nothing is available how they exactly work, but apparently very reliable systems can be built.
In active cybersecurity , haven’t found anything new where decentralisation would play a big role. Except perhaps that all parts of society are monitored with records on public blockchains. This allows real-time monitoring. If something goes awry, alarms are generated and corrective actions started. This is what private companies do all the time but nothing on community/society level (politicians do not like numeric targets that get followed in real time).
Hack back lab can also be used to test adversaries defence capabilities for discovering their weaknesses.
After
After an incident is over, Safety Inspection Boards will analyse the situation and propose actions to prevent things like that happening again.
Data being recorded to immutable storage is a post-stage activity allowing later to take deeper dives even to quite old events (what happened before, during and after; any predictive value there).